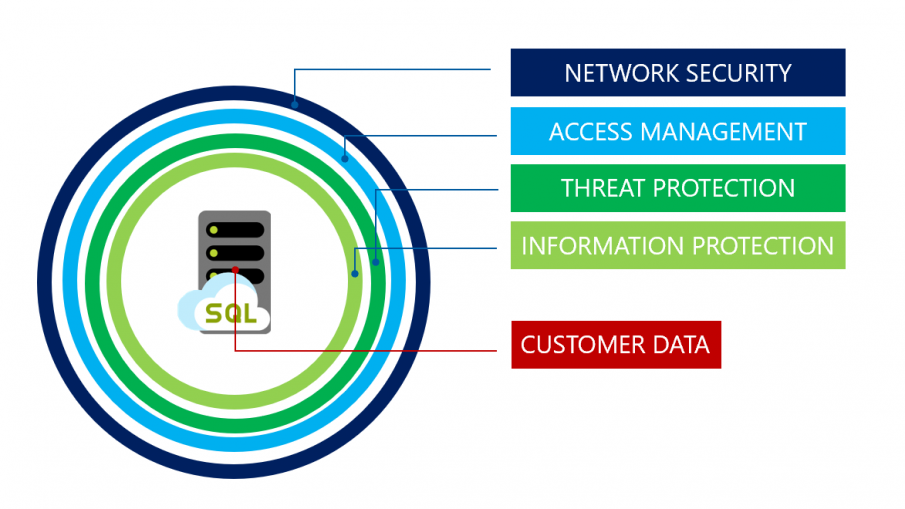
What is database security?
Database security is the process of securing privileged data from unauthorised access. It involves protecting stored data by implementing several methods like hardware and software access controls, encryption, passwords, 2-factor authentication, and system updates to ensure not just the database but the physical computer or server it is stored on is protected.
Why is it important? Common threats and challenges
Insider threats
This is one of the most common threats to database security. Many times it is the insiders that are responsible for data breaches and security lapses instead of outside threats. Starting from proper vetting and referencing of employees to restricting access to databases and physical servers or computer machines where the databases are stored play a critical role in eliminating insider threats to database security.
Human error
One of the most common threats and challenges that businesses face is human error. This can come in many different forms, such as: Users not following security protocols Using weak passwords Installing unauthorized software Opening malicious email attachments Allowing unauthorized access to systems or data Not reporting suspicious activity In order to reduce the risk of human error, it’s important to have a comprehensive security policy in place and ensure all users are aware of their responsibilities. Staff training is also essential, so employees know how to identify and report potential threats.
The exploitation of database software vulnerabilities
Software developers are under constant pressure to release new, innovative applications to meet the needs of their clients. Unfortunately, this also leaves them open to exploitation by hackers who search for vulnerabilities in the code. Once a vulnerability is found, the hacker can exploit it to gain access to private data or take over an entire system. This is why it is so important for software developers to keep up with the latest security updates and best practices.
SQL/NoSQL injection attacks
SQL/NoSQL injection attacks are a type of cyberattack that can be used to steal data or gain access to systems. They occur when hackers inject malicious code into an entry field on a web page, such as a search bar or login form, in order to get the web application to execute it. This can allow the hacker to steal data, take over the account, or damage the system.
Denial of service (DoS/DDoS) attacks
One of the most common threats to any website or even a database is a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack. This occurs when an attacker sends so much traffic to an application that in turn requests data from the database so many times that it can’t handle it, and the site goes offline. To protect against this, we use a security service that blocks malicious traffic before it reaches our servers. This service helps us keep our website and database up and running even during heavy attacks.
Malware
Malware is a general term for software that is designed to damage or disable computers and computer systems. There are many different types of malware, including viruses, worms, Trojan horses, spyware, and adware. One common way to protect against malware is to use an anti-virus program. This software can scan your computer for known malware threats and remove them. Another way to protect against malware is to have a strong security policy in place for your organization. This includes measures such as firewalls, intrusion detection systems, and anti-virus programs. Network administrators can also run scans across the network looking for misconfigured or infected devices.
Attacks on backups
Backups are essential for any database. They provide a last resort in the event of an attack that damages or destroys the primary site. However, backups are also vulnerable to attack.
Best practices
Deploy physical database security
Any computer or server can be susceptible to physical attacks by outsiders or even insider threats. Physical security measures should be deployed to protect the physical location of a database. This includes ensuring that access points are secured, keeping doors locked and off-limits to unauthorized personnel, having strict visitor policies, and limiting access to sensitive data. If a cybercriminal gets access to your physical database server, they can steal the data, corrupt it or even insert harmful malware to gain remote access. Without additional security measures, it’s often difficult to detect these types of attacks since they can bypass digital security protocols. When choosing a web hosting service, make sure it’s a company with a known track record of taking security matters seriously. It’s also best to avoid free hosting services because of the possible lack of security. If you house your own servers, adding physical security measures such as cameras, locks and staffed security personnel is highly suggested. Furthermore, any access to the physical servers should be logged and only given to specific people in order to mitigate the risk of malicious activities.
Protect Against SQL Injection
One common attack on web applications is SQL injection. In this type of attack, the attacker inserts malicious SQL statements into input fields on the web form in an attempt to access or modify data. The best way to protect against these attacks is to use parameterized queries, which are prepared statements that take user-supplied values and insert them into the query as parameters. This prevents the attacker from being able to inject arbitrary SQL code into the query.
Audit DB Logins
One common best practice for auditing database logins is to use the syslogins table in master. This table contains the login name, ID, type of account (user or group), and default database for the user. The following query returns all information from the syslogins table: SELECT * FROM syslogins; This query can be used to identify users who have a default database other than master. It can also be used to identify users who are not logging in as themselves (for example, when a user logs in as sa).
Restrict SQL Traffic
One way to restrict the amount of SQL traffic on a network is to place an appliance in the path of the traffic. This can be done in two ways: By using a proxy server that sits between the client and the database server, or By installing a software agent on each client machine.
Separate database servers and web servers
Operational data must be extracted from source systems and prepared for loading into a data warehouse. Data in a warehouse does not change constantly but rather records events or states that happened at some point in time. The goal of archiving any type of data is to preserve it for the long term and ensure its accuracy. Up to 80% of the work in building a data warehouse is devoted to the ETL process. Extracting and transforming data can be resource-intensive, so it’s important to deploy dedicated database servers and web servers specifically for this purpose. This configuration will help improve performance and decrease the amount of time required to load data into the warehouse.
Test your database security
It is important to test your database security regularly. One way to do this is by using a security service, such as CloudFlare. This will help protect your web application and database from online attacks. Additionally, you can use a DBMS tool to maintain and analyze databases. A data structure can also be helpful in organizing data for easy retrieval. Finally, it’s important to be aware of Denial-of-service (DDoS) attacks and how to prevent them from happening on your site.
Audit and continuously monitor database activity
IT audits are meant to ensure the security of an organization’s IT infrastructure. It is important for organizations to have a written audit plan that includes defined roles and responsibilities so auditors know what they are looking for during their visit to the organization. One way to help with this is by continuously monitoring database activity. This will help you identify any unauthorized changes or access, performance issues, and other problems that could affect your business-critical data. Database Archiving is a 2009 book about data warehousing and it covers themes like performance optimization, backup, disaster recovery, and migration. Database Archiving explores the theme of performance optimization in detail.
Regularly update your operating system and patches
Operating systems, such as Windows and MacOS, require updates to maintain security. These updates include patches that fix vulnerabilities discovered in the operating system. It is important to keep your software up-to-date by installing these updates regularly. If you do not install these updates, your computer may be vulnerable to attacks from hackers.
Use web application and database firewalls
Firewalls provide the first line of defence against attacks on an organization’s computer systems. Web application firewalls protect web applications from malicious traffic and database firewalls protect databases from unauthorized access. Both web application and database firewalls should be used in conjunction with each other to provide comprehensive protection for an organization’s computer systems.
Log Management and Monitoring of Traffic
Log management is the process of collecting, storing, and analyzing log data from various sources. This data can be used to help identify and resolve issues with a system or application. Log data can be used to help identify and resolve issues with a system or application. Monitoring traffic refers to the act of tracking the activity of users as they navigate through a database. This information can be used to improve user experience by identifying areas that need improvement or by detecting malicious activity. Log management and monitoring of traffic are both important aspects of cybersecurity. By implementing these measures, businesses can protect their systems and customers from harm.
Implement data encryption and masking
In order to protect your data, you should consider encrypting it. You can also mask the data so that it is not readable by unauthorized personnel. Businesses often have sensitive data that needs to be protected. In order for DevOps to be successful, this data must be secured. Encryption and masking are two effective ways of doing so.
Implement Identity Access Management (IAM)
Implementing Identity and Access Management (IAM) can be a daunting task. However, with the right approach, it can be done in a way that minimizes disruption to the business. The first step is to understand your current system(s) and business processes. This allows us to identify areas of the workflow process that could be improved. We’ll also add our own suggestions for improvement, including data, security and workflow management. Migration refers to moving the data from the old system to the new one. A prototype helps architects visualize how a system will look and feel before it’s actually built. This allows for a more efficient implementation of IAM. Three main areas that need to be considered: Who can do what? What resources can they access? Under what circumstances? To address these questions, organisations need to put in place a comprehensive and well-thought-out IAM policy. This will help ensure that employees only have access to the information and systems they need to do their jobs, and that data is protected at all times.
Data protection tools and platforms
As we all know, our data is very important to us. We want to make sure that it is properly protected and doesn’t get into the wrong hands. Luckily, there are a lot of tools and platforms out there which can help us do just that! One such platform is called “Snowflake”. It helps you move your data between different databases so that you can preserve your historical data. This is a great tool for companies who want to make sure their data is always safe and sound. Another popular platform is called “Hadoop”. Hadoop was created by Yahoo! and it allows you to store a vast amount of data in a scalable manner. This makes it perfect for companies who need to keep track of a lot of information. Finally, another tool which can be used for data protection is called “DataStax Academy”. DataStax Academy provides users with the ability to learn about big data technologies like Cassandra and Spark. This is a great option for people who want to become experts in big data security.